How-to: Set up SAML authentication with ADFS in Expensify

Please note you will need to be using a group policy on a Control plan as well as a verified Domain in order to set up this feature.
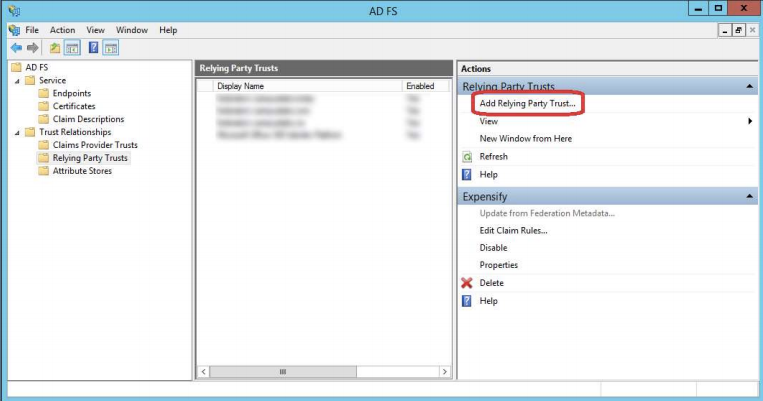
- Open the ADFS management console, and click the ‘Add Relying Party Trust’ link on the right.
2. Check the option to ‘Import data about the relying party from a file’, then click the ‘Browse’ button. What this is expecting is the XML file of Expensify’s metadata. (You can create such a file from the Expensify SAML setup page. Just copy/paste the metadata into a new text file, and save the file with an XML extension.)
Locate the file, the click Next.
3. The metadata file will provide the critical information that ADFS needs to set up the trust. Give it a name, and click Next.
4. Leave the option to permit all users, then click Next.
5. The next step will give you an overview of what is being configured. Click Next.
6. The new trust is now created. Highlight the trust, then click ‘Edit claim rules’ on the right.
7. Click 'Add a Rule':
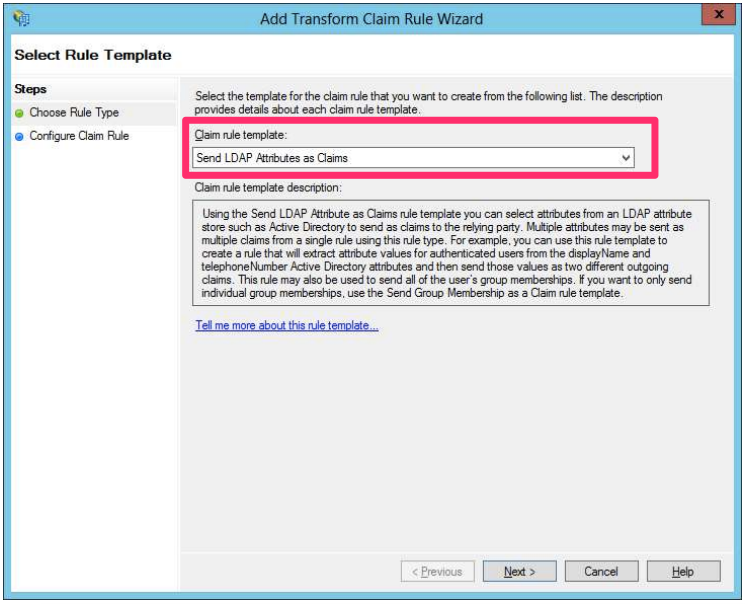
8. The default option should be ‘Send LDAP Attributes as Claims’. Click Next.
9. Note: Depending upon how your Active Directory is set up, you may or may not have a useful email address associated with each user, or you may have a policy to use the UPN as the user attribute for authentication. If so, using the UPN user attribute may be appropriate for you. If not, you can use the emailaddress attribute.
Give the rule a name like “Get email address from AD”. Choose Active Directory as the attribute store from the dropdown list. Choose your source user attribute to pass to Expensify that has users’ email address info in it, usually either
“E-Mail-Address” or “User-Principal-Name”. Select the outgoing claim type as “E-Mail Address”. Click OK.
10. Add another rule; this time, we want to “Transform an Incoming Claim”. Click Next.
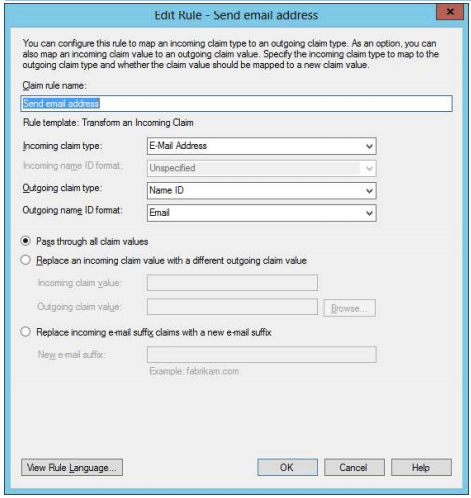
11. Name the rule “Send email address”. The Incoming claim type should be “E-Mail Address”. The outgoing claim type should be “Name ID”, and the outgoing name ID format should be “Email”. Click OK.
12. You should now have two claim rules, shown below.
Assuming you’ve also set up Expensify SAML configuration with your metadata, SAML logins on Expensify.com should now work.
ADFS’ default metadata path is:
https://yourservicename.yourdomainname.com/FederationMetadata/2007-06/FederationMetadata.xml